**Concise Description:** Self-hosted zero trust access platform. VPN, ZTNA, API gateway, PaaS, and secure remote access solution. #zerotrust #security #opensource
# Octelium: Model Context Protocol (MCP) Gateway and Zero Trust Access Platform
[](https://opensource.org/licenses/Apache-2.0)
[](https://www.gnu.org/licenses/agpl-3.0)
[](https://octelium.com/external/discord)
[](https://octelium.com/external/slack)
<div align="center">
<br />
<img src="./unsorted/logo/main.png" alt="Octelium Logo" width="350"/>
<h1>Octelium</h1>
</div>
## Table of Contents
- [Introduction](#introduction)
- [Key Features](#key-features)
- [MCP Gateway Functionality](#mcp-gateway-functionality)
- [Use Cases](#use-cases)
- [Getting Started](#getting-started)
- [Try Octelium in a Codespace](#try-octelium-in-a-codespace)
- [Install CLI Tools](#install-cli-tools)
- [Install your First Cluster](#install-your-first-cluster)
- [Useful Links](#useful-links)
- [License](#license)
- [Support](#support)
- [Frequently Asked Questions](#frequently-asked-questions)
- [Legal](#legal)
## Introduction
Octelium is a free and open-source, self-hosted, unified platform for zero-trust resource access. It serves as a modern alternative to remote access VPNs and ZTNA solutions. Beyond traditional VPN and ZTNA use cases, Octelium provides a scalable infrastructure for secure tunnels, API gateways, and, critically, **MCP (Model Context Protocol) gateways**. It also functions as a PaaS-like platform for secure containerized application hosting, a Kubernetes gateway, and even a homelab infrastructure.
Octelium provides a scalable zero-trust architecture (ZTA) for identity-based, application-layer (L7) aware, secret-less secure access. This access is facilitated through both private client-based access over WireGuard/QUIC tunnels and public clientless access (i.e., BeyondCorp). It caters to both human users and workloads, granting access to any private/internal resource behind NAT in any environment, as well as to publicly protected resources such as SaaS APIs and databases via context-aware access control on a per-request basis through policy-as-code.
## Key Features
* **Unified Zero Trust Architecture:** A modern, scalable architecture built on identity-aware proxies (IAPs) for application-layer access control, rather than network-level segmentation.
* Unified access platform for humans and workloads.
* Unified architecture for accessing private/internal resources behind NAT and protected public resources.
* Supports both client-based (WireGuard/QUIC) and clientless (BeyondCorp) access methods.
* Built on Kubernetes for automatic horizontal scalability and availability.
* **Dynamic Secret-less Access:** Eliminates the need to manage and share long-lived, over-privileged secrets for accessing protected resources. Supports:
* HTTP-based resources (APIs, web apps).
* SSH.
* Kubernetes clusters.
* PostgreSQL and MySQL databases.
* Applications protected by mutual TLS (mTLS).
* **Context-Aware, Identity-Based Access Control:** Fine-grained, dynamic access control on a per-request basis using modular and composable *Policies* written as code using CEL or OPA.
* **Context-Aware Dynamic Configuration and Routing:** Route requests to different upstreams based on policies defined using CEL or OPA.
* **Continuous Strong Authentication:** Supports various identity providers (IdPs) via OpenID Connect, SAML 2.0, and GitHub OAuth2. Also supports "secret-less" authentication for workloads using OIDC-based assertions.
* **OpenTelemetry-Ready Auditing and Visibility:** Logs every request and exports them in real-time to OpenTelemetry OTLP receivers for integration with log management and SIEM tools.
* **Effortless Password-less SSH Access:** Clients can serve SSH even when not running as root, enabling SSH access to containers and IoT devices.
* **Effortless Containerized Application Deployment:** Provides PaaS-like capabilities to deploy, manage, and scale containerized applications as *Services*.
* **Centralized, Declarative, and Programmable Management:** Administered declaratively like Kubernetes, using the `octeliumctl` CLI tool. Fully programmable via gRPC-based APIs.
* **No Infrastructure Changes Required:** Upstream resources do not need to be aware of Octelium.
* **Avoids Traditional VPN Networking Problems:** Client-based private networking eliminates routing conflicts and simplifies dual-stack networking.
* **Open Source and Self-Hosted:** Designed for single-tenant self-hosting with no vendor lock-in.
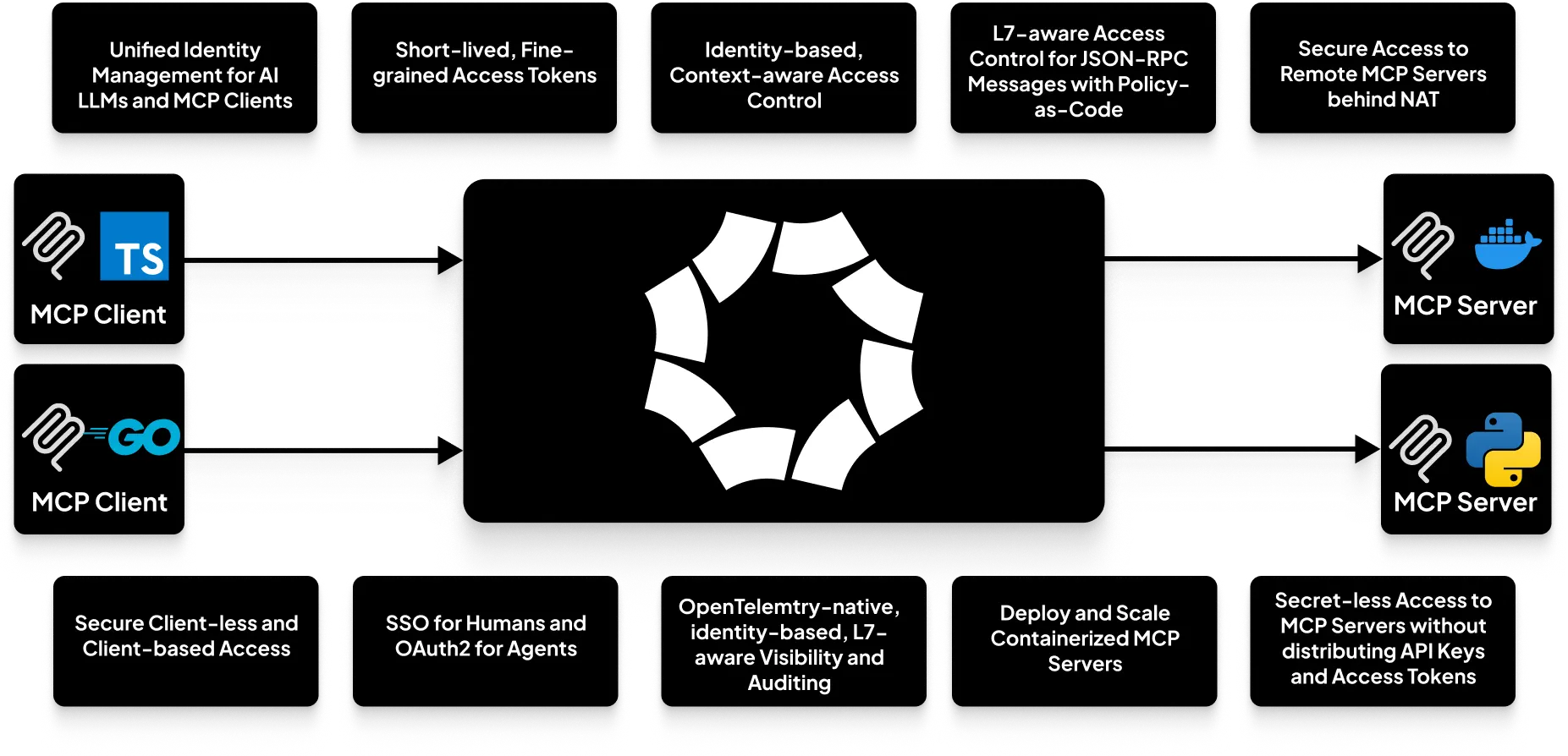
## MCP Gateway Functionality
Octelium provides a secure infrastructure for Model Context Protocol (MCP) gateways and Agent2Agent Protocol (A2A)-based architectures. This includes:
* **Identity Management:** Securely manages identities for MCP agents.
* **Authentication:** Supports authentication over standard OAuth2 client credentials and bearer authentication.
* **Secure Remote Access and Deployment:** Enables secure remote access and deployment of MCP agents.
* **Identity-Based Access Control:** Provides L7-aware access control via policy-as-code for MCP agents.
* **Visibility:** Offers visibility into MCP agent interactions.
**Example:** See a self-hosted MCP example [here](https://octelium.com/docs/octelium/latest/management/guide/service/ai/self-hosted-mcp).
## Use Cases
Octelium is designed to be generic enough to be used as a solution for various use cases, including:
* **Modern Remote Access VPN:** A zero-trust alternative to traditional VPNs.
* **Unified ZTNA/BeyondCorp Architecture:** A Zero Trust Network Access (ZTNA) platform.
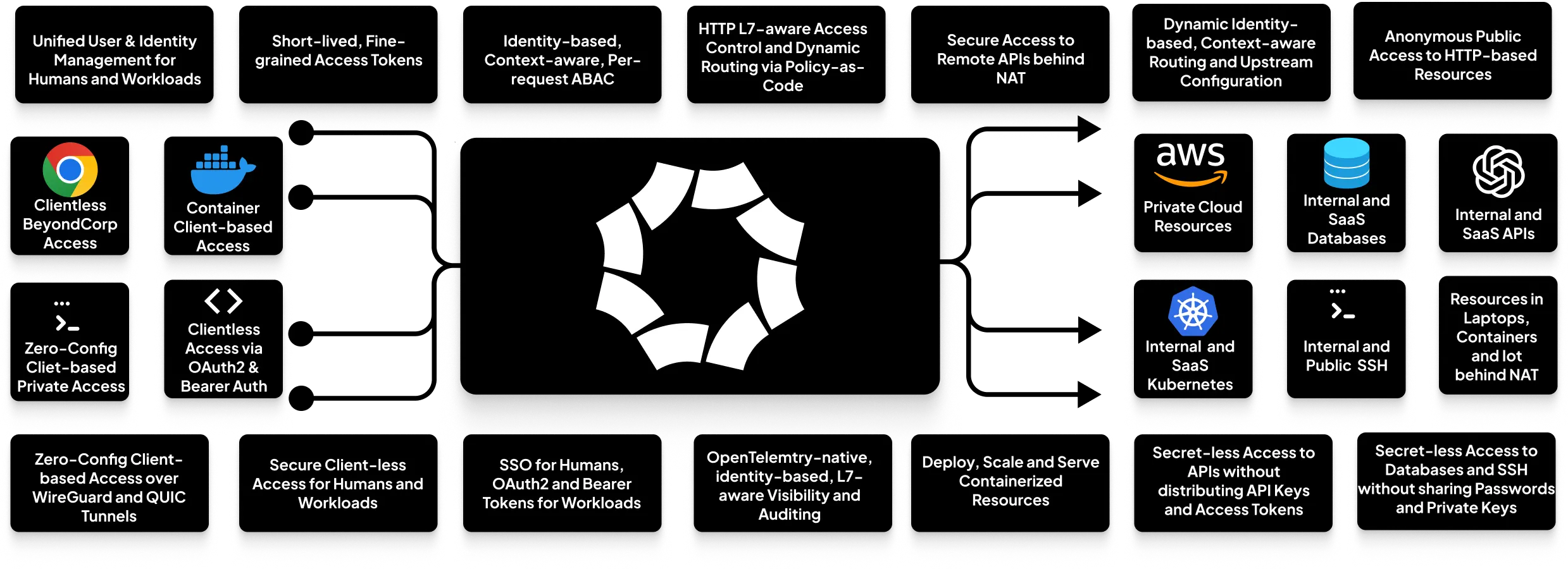
* **Self-Hosted Infrastructure for Secure Tunnels:** A self-hosted secure tunnels and reverse proxy programmable infrastructure. See an example [here](https://octelium.com/docs/octelium/latest/management/guide/service/http/open-source-self-hosted-ngrok-alternative).
* **Self-Hosted PaaS:** A scalable platform to deploy, scale, and host containerized applications. See examples for [Next.js/Vite apps](https://octelium.com/docs/octelium/latest/management/guide/service/http/nextjs-vite), [remote VSCode](https://octelium.com/docs/octelium/latest/management/guide/service/homelab/remote-vscode-code-server), [remote Ollama](https://octelium.com/docs/octelium/latest/management/guide/service/ai/remote-ollama) and [Pi-hole](https://octelium.com/docs/octelium/latest/management/guide/service/homelab/pihole).
* **API Gateway:** A self-hosted, scalable, secure API gateway. See an example [here](https://octelium.com/docs/octelium/latest/management/guide/service/http/api-gateway).

* **AI Gateway:** A scalable AI gateway to any AI LLM providers. See an example [here](https://octelium.com/docs/octelium/latest/management/guide/service/ai/ai-gateway).
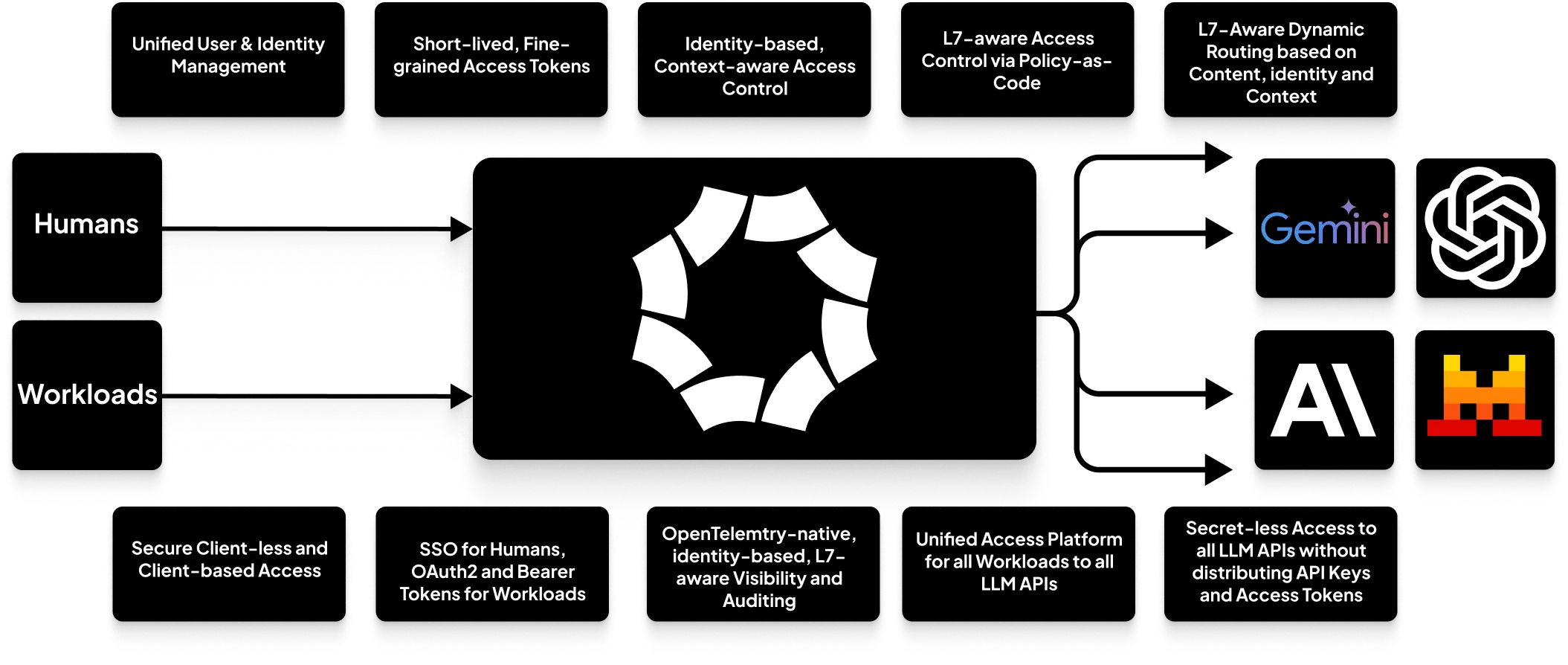
* **Unified Zero Trust Access to SaaS APIs:** Secure access to HTTP-based SaaS APIs.
* **MCP Gateways and A2A-Based Architectures:** A secure infrastructure for Model Context Protocol (MCP) gateways. See an example [here](https://octelium.com/docs/octelium/latest/management/guide/service/ai/self-hosted-mcp).

* **Kubernetes Ingress Alternative:** A more advanced alternative to Kubernetes Ingress and load balancers.
* **Homelab:** A unified self-hosted Homelab infrastructure.
## Getting Started
### Try Octelium in a Codespace
You can